TLDR
- DeFi protocol Li.Fi was hacked for approximately $11 million in Ethereum and stablecoins.
- The exploit targeted users who had manually set infinite approvals on their accounts.
- Li.Fi has contained the exploit and says users are no longer at risk.
- The attack may have exploited a vulnerability in the Li.Fi bridge.
- This is not the first security issue for Li.Fi, which lost $600,000 in a 2022 incident.
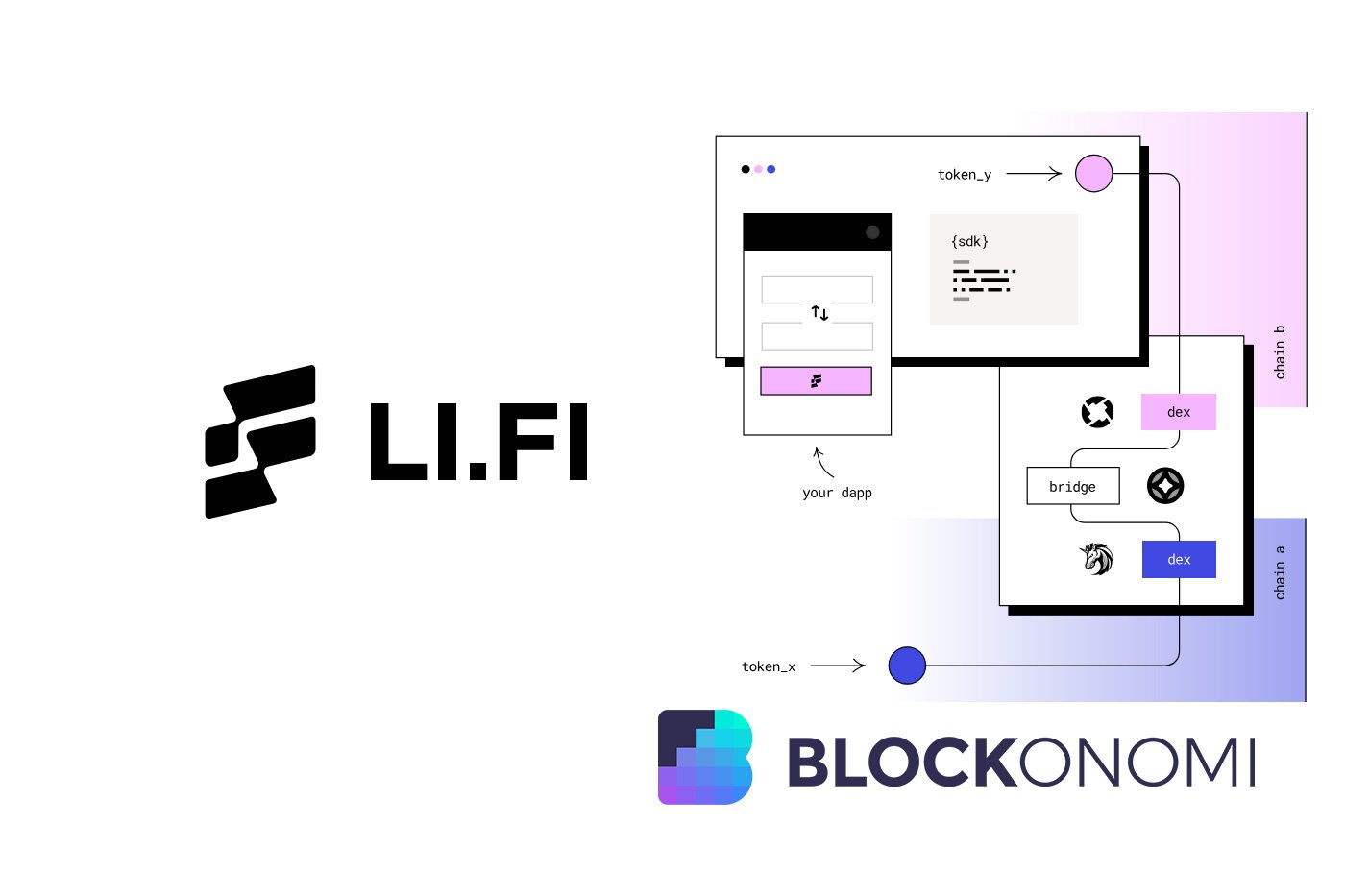
On July 16, 2024, the cross-chain decentralized finance (DeFi) protocol Li.Fi suffered a significant security breach. Hackers managed to exploit a vulnerability in the system, resulting in the loss of approximately $11 million worth of cryptocurrencies.
The stolen funds primarily consisted of Ethereum (ETH) and various stablecoins, including USDC, USDT, and DAI. Blockchain security firm CertiK initially reported the loss at nearly $9 million, but Li.Fi later confirmed to Decrypt that the total amount stolen was closer to $11 million.
🚨ALERT🚨@lifiprotocol, Our system has raised suspicious transactions involving your https://t.co/3LzbDK99Ed
We recommend users to revoke their approvals for: 0x1231deb6f5749ef6ce6943a275a1d3e7486f4eae
More than $8M have been drained so far from users and mostly stablecoins!… pic.twitter.com/zsj9DZWnpU
— 🚨 Cyvers Alerts 🚨 (@CyversAlerts) July 16, 2024
Li.Fi, which allows users to trade across different blockchains, venues, and bridges, quickly responded to the incident. The protocol’s team announced on social media platform X (formerly Twitter) that they were investigating a potential exploit and urged users not to interact with any Li.Fi-powered applications until further notice.
According to Li.Fi, the exploit appears to have targeted users who had manually adjusted their account settings to allow “infinite approvals.” This setting essentially gives a smart contract unlimited access to a user’s funds, which can be risky if the contract is compromised.
A smart contract exploit earlier today has been contained and the affected smart contract facet disabled.
There is currently no further risk to users.
The only wallets affected were set to infinite approvals, and represented only a very small number of users.
We are engaging…
— LI.FI (@lifiprotocol) July 16, 2024
Crypto security firm Decurity suggested that the root cause of the exploit was likely a vulnerability in the Li.Fi bridge. They pointed to a specific function in a smart contract that was deployed just five days before the attack, which allowed for “arbitrary call with user-controlled data.”
https://t.co/k9LgVmliv7 bridge was exploited for ~8M USD.
The root cause is a possibility of an arbitrary call with user controlled data via `depositToGasZipERC20()` in GasZipFacet which was deployed 5 days ago!
One of hack txs: https://t.co/ILPFpZnJH8 pic.twitter.com/qpTmyFnCx8
— Decurity (@DecurityHQ) July 16, 2024
Li.Fi has since contained the exploit and disabled the affected smart contract facet. The protocol assured users that there is currently no further risk, emphasizing that only a small number of users who had set infinite approvals were affected.
In response to the incident, Li.Fi advised users to immediately use their “secluded revoke website” and provided a list of specific addresses that should be revoked. They also recommended that users visit scan.li.fi to check if their accounts have been compromised.
This is not the first time Li.Fi has faced security issues. In 2022, a bug in the protocol’s swapping feature resulted in losses of $600,000 in cryptocurrency. The recurring nature of these incidents highlights the ongoing security challenges faced by DeFi protocols.
The Li.Fi hack contributes to a growing tally of crypto thefts in 2024. According to a report by blockchain intelligence firm TRM Labs, hackers stole more than twice as much cryptocurrency in the first half of 2024 compared to the same period in 2023.
The total value of crypto thefts reached $1.38 billion by June 24, 2024, nearly matching the $1.7 billion stolen across all of 2023.
Li.Fi’s team stated that they are engaging with law enforcement authorities and relevant third parties, including industry security teams, to trace the stolen funds. They have promised to issue a more detailed post-mortem analysis of the incident as soon as possible.